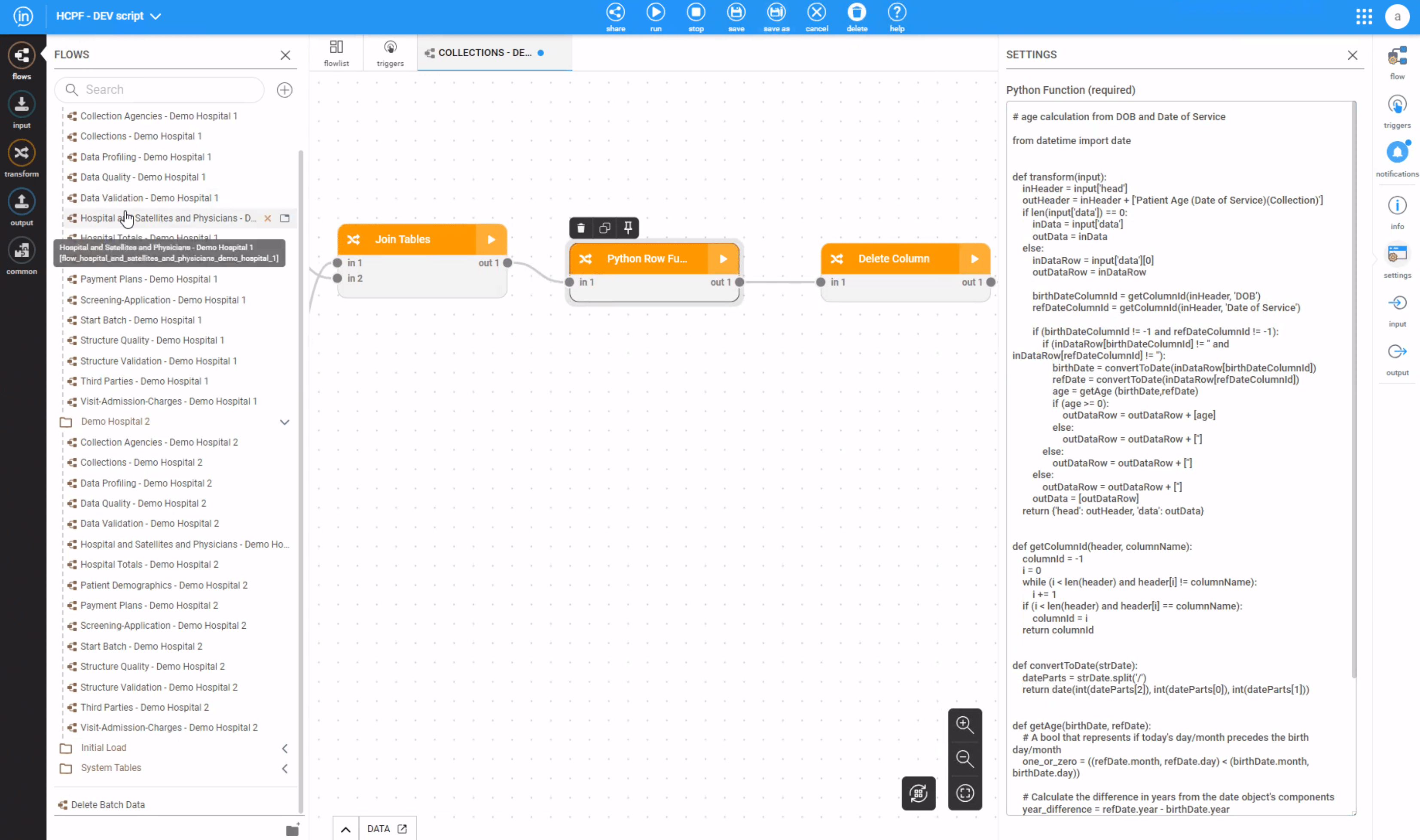
The Inzata security and privacy system is a comprehensive solution that offers a wide range of features to ensure the safety and security of your data. It is fully certified in compliance with HIPAA and SOC2 standards, making it an ideal solution for healthcare and financial industries that require a high level of security for their sensitive data.
One of the key features of Inzata is its utilization of the state-of-the-art data security layers of AWS, Google, and Azure cloud infrastructure. This guarantees that the latest and most advanced security technologies protect your data, offering an unparalleled level of protection. Additionally, Inzata incorporates common principles of role-based settings with Access Control Lists (ACL) for advanced authentication and authorization. This enables you to have complete control over who has access to your data and at what level.
Role-Based Data Filtering and Access Control
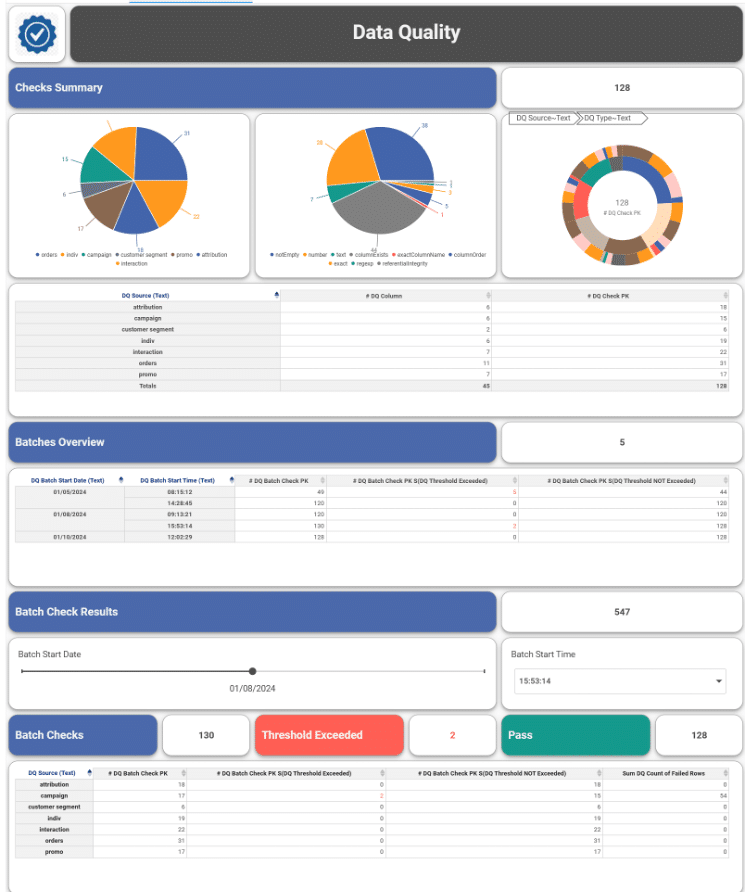
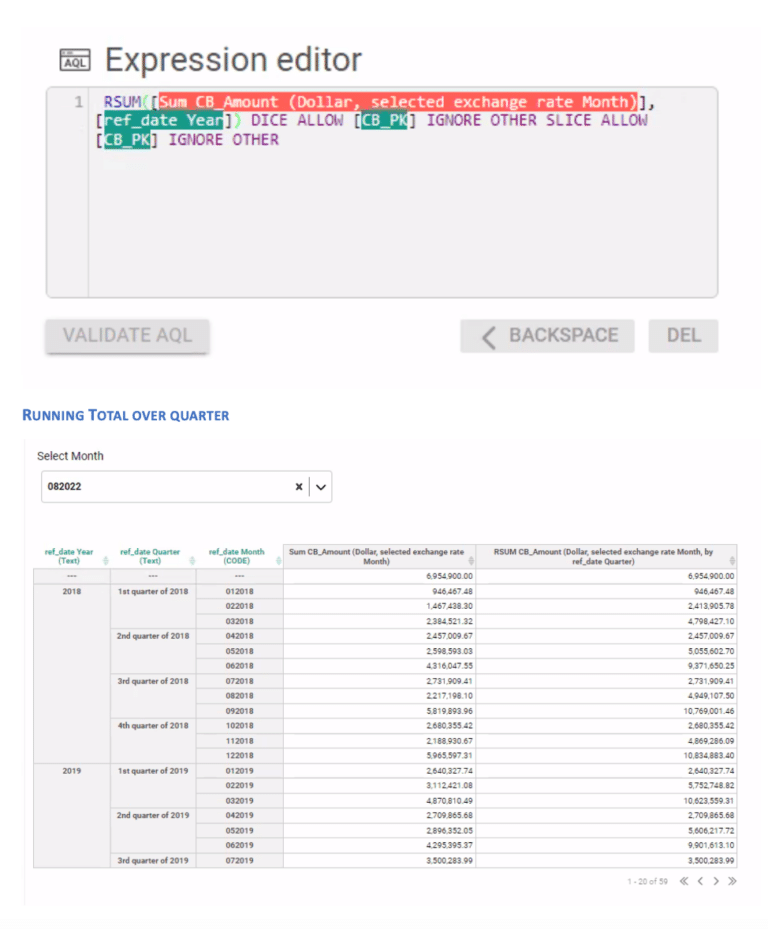
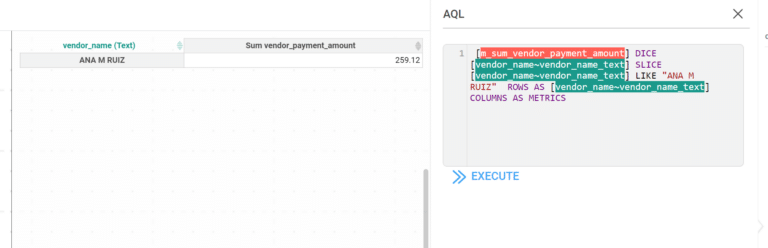
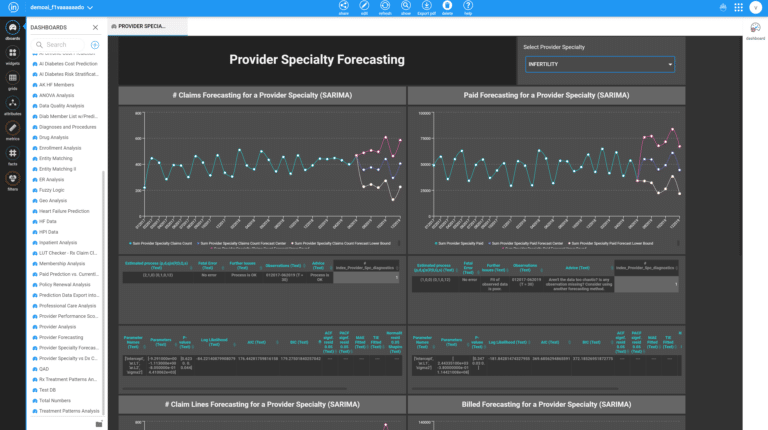
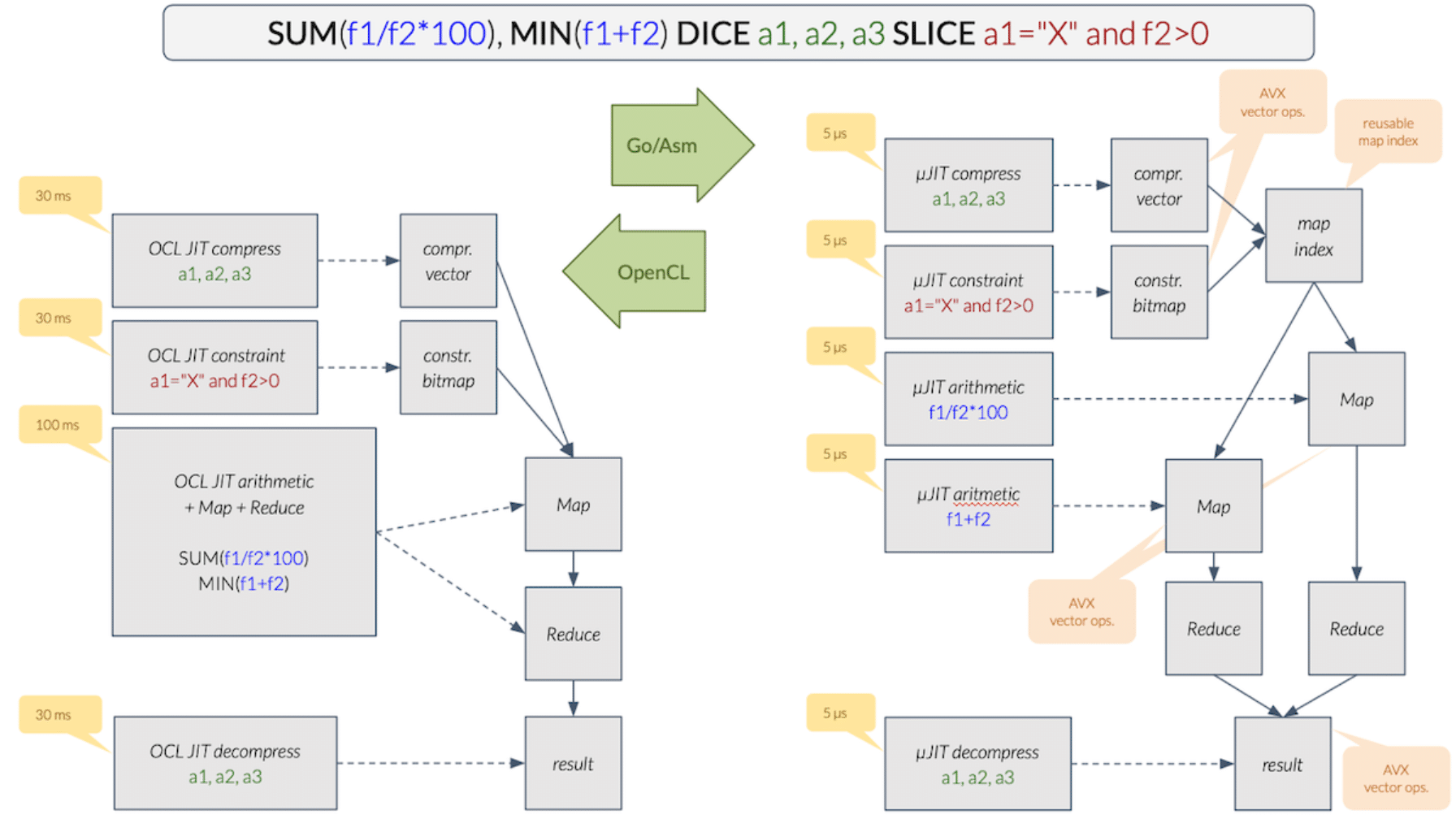
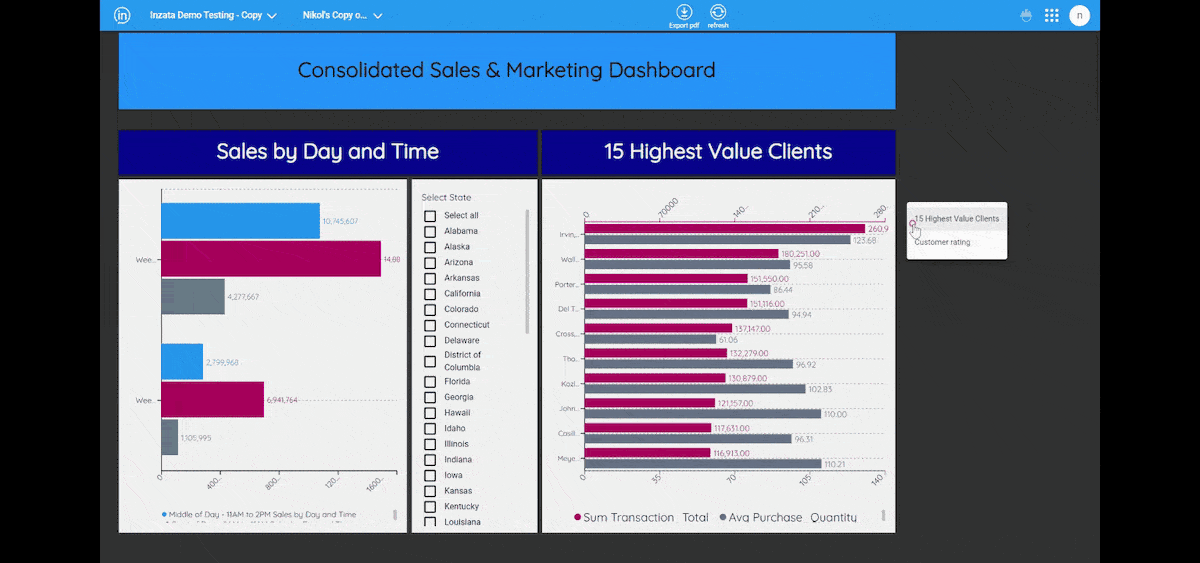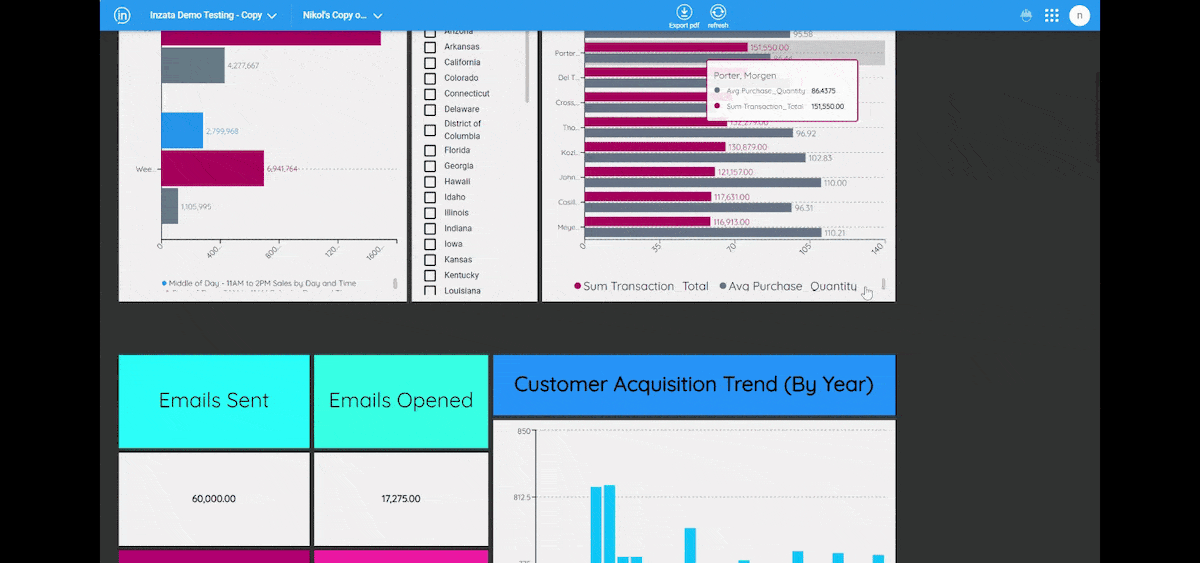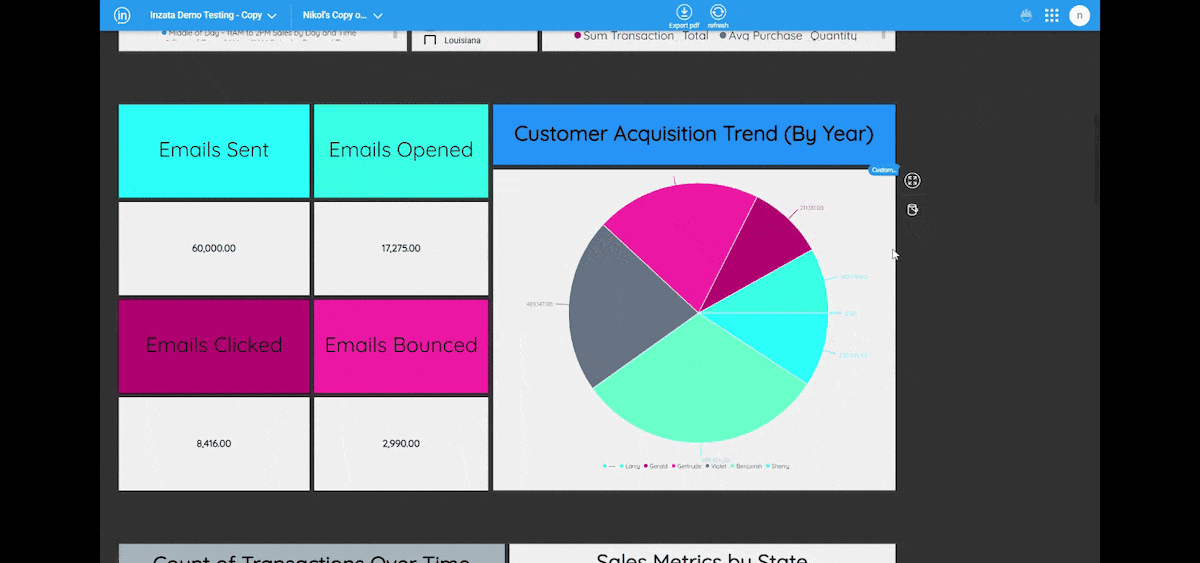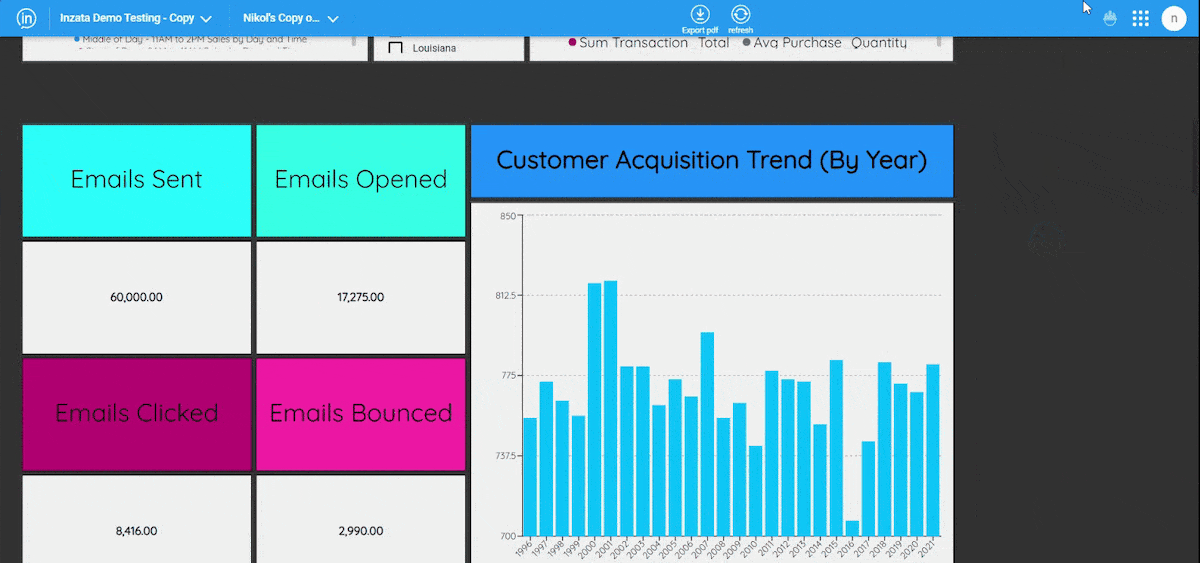
Inzata also offers powerful role-based filtering of data through security filters. This feature guarantees that it restricts unauthorized users from accessing certain data in the reports they lack authorization for, thereby ensuring that only authorized personnel can access sensitive information. It also allows roles to be associated with each user, adding an extra layer of security. Additionally, Inzata security filters automatically apply at any aggregation level, including when drilling down to the atomic data level. This guarantees that your data remains secure even when drilling down to the most granular level.
The access Control List system allows each object to set a definition by a user role and basic access methods, including read and write rights. This enables you to set specific access privileges for different objects, such as filters, reports, dashboards, metrics, facts, and attributes. This ensures that only authorized personnel can access specific objects and perform specific actions on them.
Monitoring, Alerts, and Audit Logging for Enhanced Security
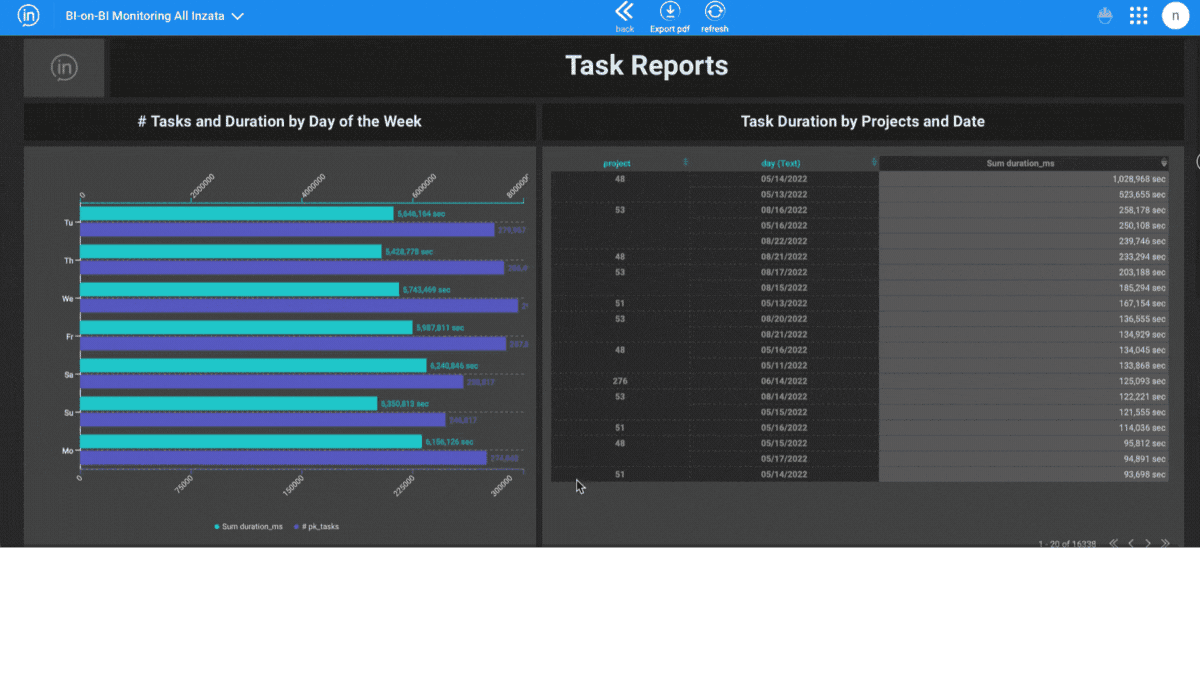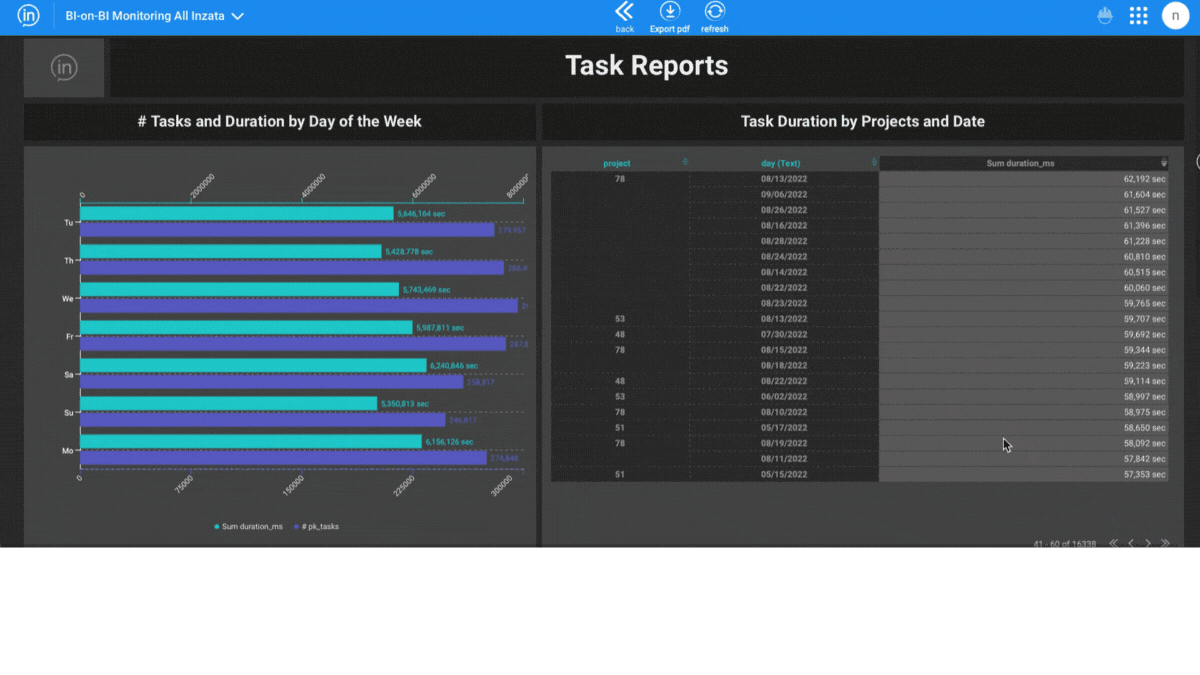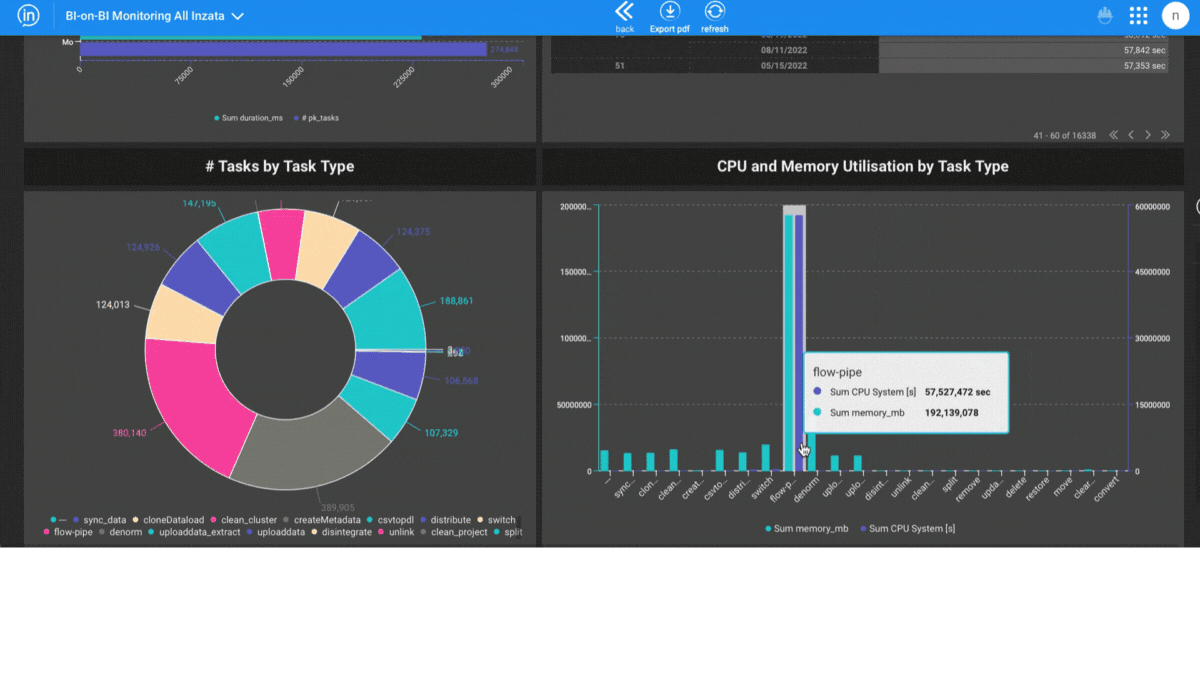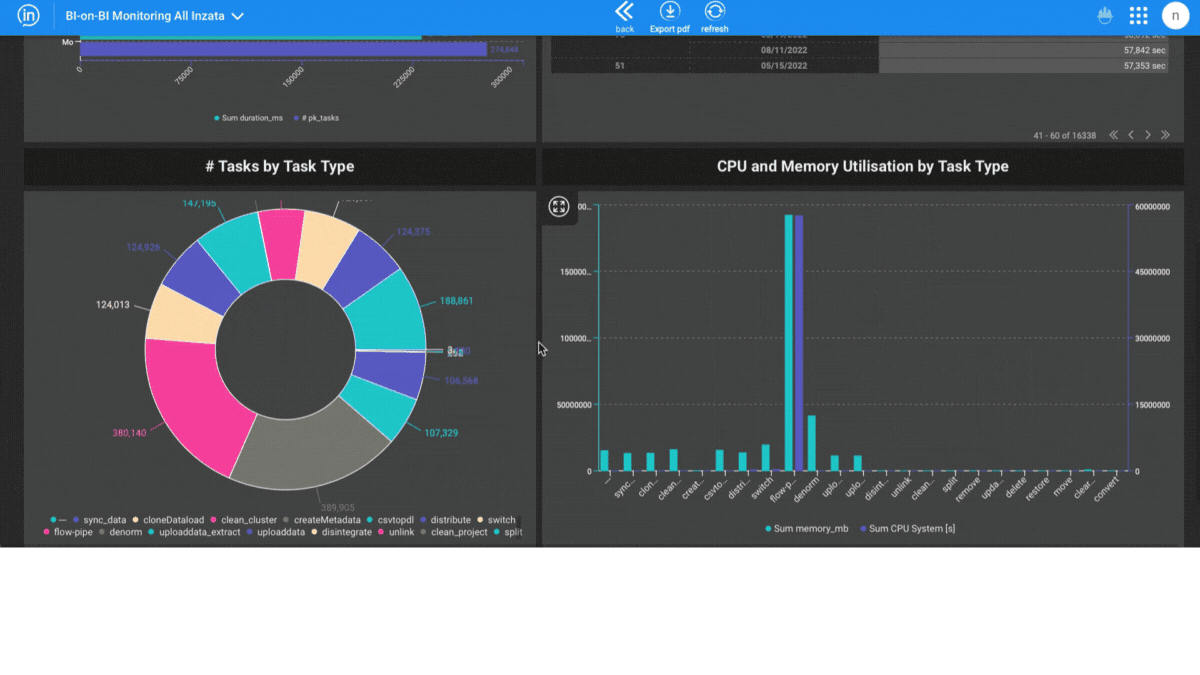
Inzata also offers real-time monitoring and alerts. This helps you stay informed about any potential security breaches or suspicious activity on your data. Additionally, it includes a built-in audit logging capability. This feature keeps records of all actions performed on your data. It provides you with a complete history of who has accessed your data and when.
Inzata’s advanced security features, combined with its compliance with industry standards, make it an ideal solution for protecting your sensitive data. With Inzata, you can trust that your data is secure and protected at all times. This gives you peace of mind, knowing that your data is safe and secure.